SL5 discussion, timeline, collection of links
Jan 17 photos of card and listing of pins.
Feb 3 search for alternative entry points, discussion aborted.
Feb 3 resilient hook should intercept card firmware every time...even if ROM isn't unlocked! (Bonus Get Smart clip)
Jan 17 address line mapping from bus to EPROM.
Jan 21 snippet of scrambled ROM dump.
Jan 20 description of card's original condition, anti-piracy role, tamper-resistance.
Jan 20 listing of C400 in comment format.
Jan 18 raw EPROM dump as unknown_2716.bin
Jan 18 conjectures about EPROM data rot.
Jan 25 histogram of EPROM byte values, puzzle-style "Rosetta Stone" descramble attempt, spreadsheet-style mapping
Jan 25 cross-reference to Apple's prescribed ROM circuit, not yet grasping that the card adds a "lock" circuit.
Jan 20 C400 ROM disassembly posted as text file.
Jan 20 various guesses by various users, pics of annotated firmware, pics of other anti-piracy cards, pics of annotated "reset-and-disassemble" routine. No success.
Jan 25 plausible candidate of descrambled EPROM (from Rosetta Stone puzzle), mapping diagram for all but A8 A9 A10, annotated listing of Applesoft descramble program, snippet of "secret handshake" tokens
Jan 26 ten step story-like conjecture on how the card might have been used.
Jan 20 early notes on card's token parsing, partly-annotated code, bad guess that it might be an Applesoft extension of some kind.
Feb 3 cloned card's firmware into another card,
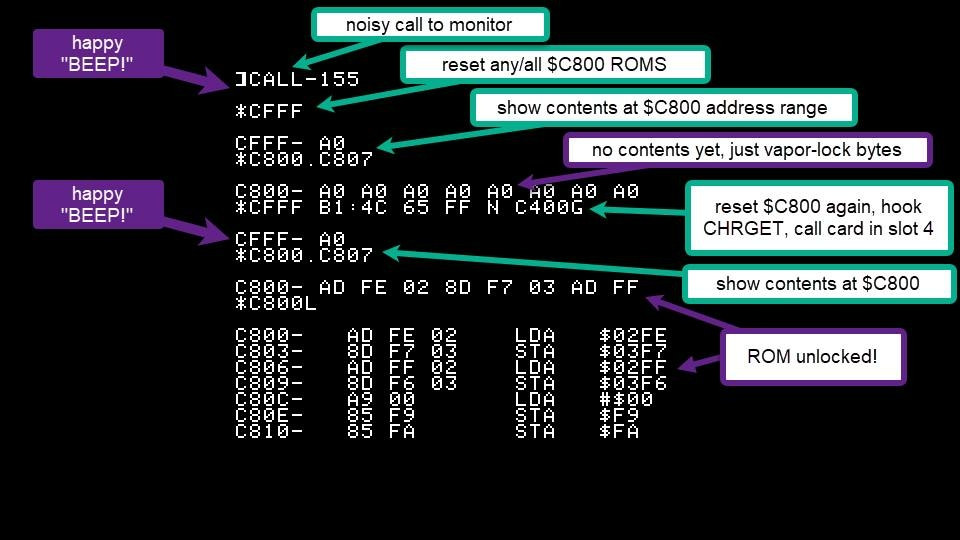
Feb 4 card unlocked attempt
This is it...I hope...!
These commands should permit the card to unlock its ROM, but always send it to the monitor before it can do a memory-wipe or lock itself again.
Test edit: I am inserting an audio media object below, just to test the blogpost editor
- S.Elliott's blog
- Log in or register to post comments